There is no limit to the interest and attraction many people have about encryption. Let us know the details about encryption. In this post you will know:
- Encryption key
- How encryption works
- Why encryption is important
- Disadvantages of encryption
What is encryption?
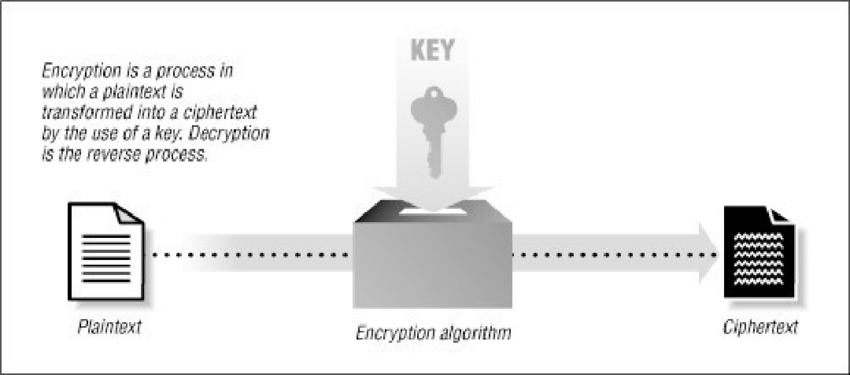
Encryption is the process by which a file is converted to a format that can only be accessed with secret code or decryption keys. It provides security to sensitive information.
Users’ personal information is stored online on various websites and servers. And this data is not stored directly in plain text language but is saved in a pattern that can only be viewed using decryption keys. In other words, encryption is the element of protecting the security of various information online or offline. Through encryption, the information is turned into scattered data which cannot be seen. But it is possible to recreate that encrypted information using a specific “decryption key”. The opposite of encryption is “decryption”.
How does encryption work?
Encryption is the process by which plain text, such as email or text messages, is converted to an unreadable format, called “cipher text.” Encryption is used to protect the privacy of digital data stored on a computer or sent or stored on the Internet.
When a message sent using encryption reaches the desired person, it becomes normal. Both the sender and the receiver have a secret encryption key to unlock this message, which works automatically.
Types of encryption
Different types of encryption have been created keeping in mind the different needs and security. Let’s take a look at some popular encryption examples.
Data encryption standard
Data encryption standard or DES is a basic-level encryption standard. IBM designed it in the 1980s. Technological advances and hardware depreciation have weakened the delivery of sensitive data. It is a 56 bit encryption technology.
Triple DES
Triple DES basically uses three 56 bit keys which provide 3 times more protection than the original DES. However, at present it is not being used very much.
3 To follow Fulcrumy site in Google News Click here then follow 33
RSA
RSA is an encryption system based on the first letter of the name of three computer scientists (Rivest-Shamir-Adleman), which uses powerful and popular encryption. It is widely used for secure data exchange.
Advanced Encryption Standard (AES)
The Advanced Encryption Standard, or ES, is an encryption method used by the United States government, first published in 1997. It is widely used worldwide.
Tufish
Tufish is one of the fastest encryption algorithms and in many cases it is a little faster than others. As it is free, anyone can use it for free software and hardware.
SSL
Most websites provide “Secure Sockets Layer” or SSL protection by encrypting data. This protects the website from data leaks in transit.
Having a padlock icon in the URL bar after entering a website and having https: // s means that the website is using encryption technology. This means that no one else will be able to see the information that is coming to you from this site and the information that is going to this site from you. Internet service providers will not get that information either.

Why encryption is important
Encryption is a very important issue in the world of internet. Let’s learn about the importance of encryption.
Internet privacy
Through encryption, personal information is not displayed to anyone other than the desired person / device. The highest level of protection is achieved using encryption technology.
But you have to make sure of this yourself. The first condition of online privacy is to ensure that emails are sent using an encrypted connection.
Almost every email client’s settings have different settings for encryption. If you check your mail from a web browser, it is your responsibility to make sure that the website has SSL encryption after the visit.
3 Is it ok to use more than one antivirus?
Hacking a business
Cybercrime, driven by multiple international organizations, has now become a global business. Large scale data leaks are caused in many cases due to the ineffectiveness of this encryption technology.
Law enforcement
It is the duty of the citizens of the state to comply with the rules and standards of law by using encryption. It is also used for the purpose of data security of customers.
3 What to do if you forget your Facebook password
3 What is Linux? What are the advantages of Linux based operating system?
Difficulty of encryption
Although designed to protect our data, encryption can be used against us if desired.
Cybercriminals lock devices with encryption and demand money – a phenomenon of ransomware but not new. This ransomware is capable of causing harm not only to individuals but also to organizations. Ransomware attacks are also often carried out on certain computers.
Attackers try to encrypt various types of devices, including computers and servers, by inserting ransomware into the system. Occasionally there is a demand for ransomware before providing encrypted data encryption keys.
So, we have learned about how encryption works. We also learned about different types of encryption. What do you think about encryption? Let us know in the comments section.
[★★] Want to write about technology? Now one Technician Open an account and post about science and technology! fulcrumy.com Create a new account by visiting. Become a great technician!